Wide Multi Channel Presentation Attack (WMCA)
Database Description | Presentations | Evaluation | File Naming Convention
Introduction
The Wide Multi Channel Presentation Attack (WMCA) database consists of 1941 short video recordings of both bonafide and presentation attacks from 72 different identities. The data is recorded from several channels including color, depth, infra-red, and thermal.
The preprocessed version of the dataset with grayscale, depth, infrared and thermal and the preprocessed version of the dataset with only RGB channels are available for download.
Additionally, the pulse reading data for bonafide recordings is also provided.
Preprocessed images for some of the channels are also provided for part of the data used in the reference publication.
The WMCA database is produced at Idiap within the framework of “IARPA BATL” and “H2020 TESLA” projects and it is intended for investigation of presentation attack detection (PAD) methods for face recognition systems.
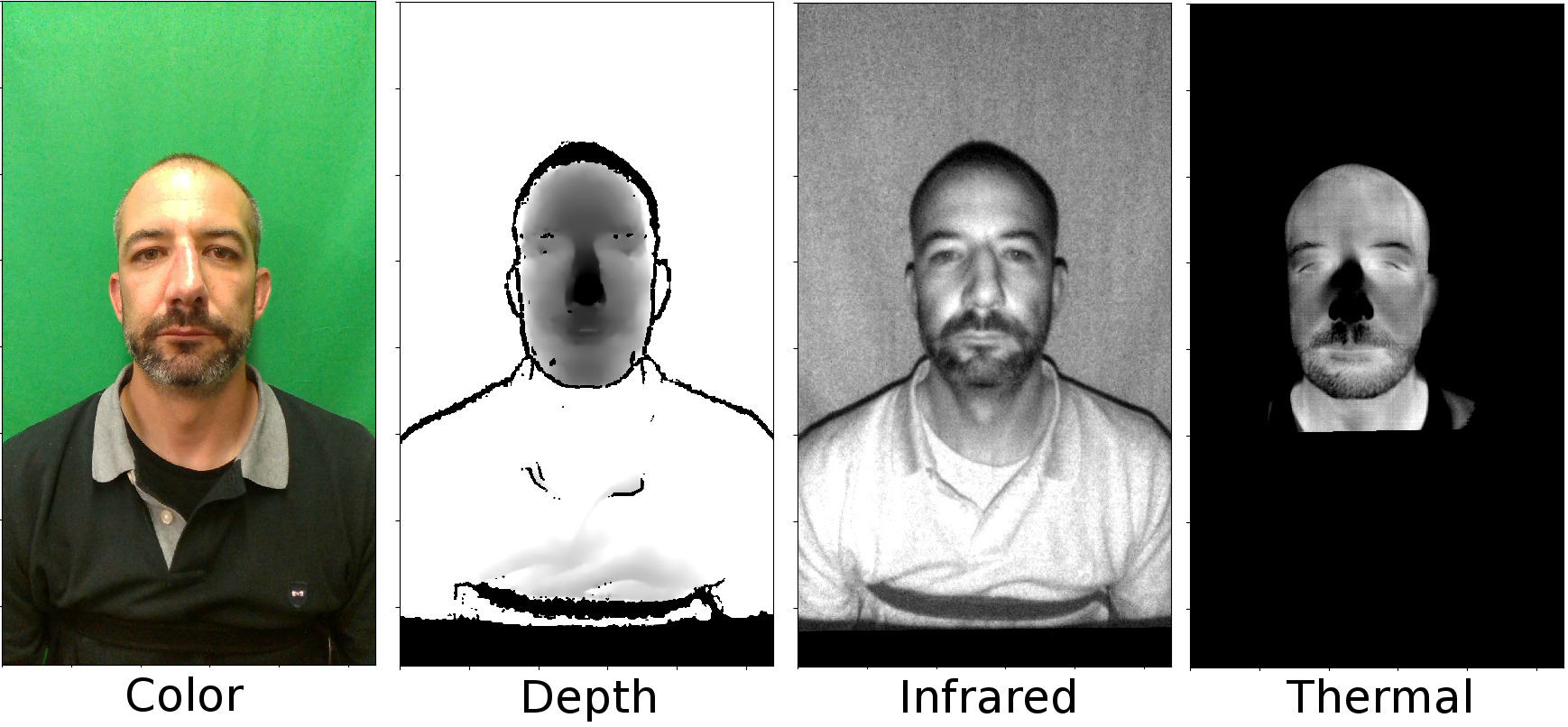
Figure 1.1: Sample images of bonafide from the database for four channels after alignment. The images from all channels are aligned with the calibration parameters and normalized to eight bit for better visualization.
Access the WMCA database
The preprocessed version of the database is available for download free of charge.
The full version of WMCA dataset (4.7T) can be ordered on encrypted hard drive for a fee
To order the full dataset, please contact our data manager.
Reference
If you use this database, please cite the following publication:
Anjith George, Zohreh Mostaani, David Geissbühler, Olegs Nikisins, André Anjos, Sébastien Marcel, "Biometric Face Presentation Attack Detection with Multi-Channel Convolutional Neural Network", in IEEE Transactions on Information Forensics and Security, 2019.
https://publications.idiap.ch/index.php/publications/show/4077
Database Description
The image data from different channels were captured with the following sensors.
1. “Intel RealSense SR300” which captures the color, depth, and infra-red channels.
2. “Seek Thermal Compact PRO” which captures data from thermal channel.
3. “Xenics Gobi-640-GigE” that captures high quality thermal images.
4. “uEye SE USB2.0” that captures high quality infra-red images.
From the mentioned sensors the “Intel RealSense SR300”, “Seek Thermal Compact PRO”, and “Xenics Gobi-640-GigE” captures data synchronously during 10 seconds. The data from “uEye SE USB2.0” is captured during 10 seconds after the first three sensors finished their data acquisition and a LED ring is switched on providing NIR illumination.
The pulse reading from only real access data was captured at the same time as the first three sensors and it is saved in a “.txt” file with the same name. This data can be used in remote photoplethysmography (rPPG) studies for face PAD. A Blood-Volume Pulse (BVP) sensor and a respiration belt was used to collect the data.
5. BVP model “SA9308M” and respiration belt model “SA9311M”, both from Thought Technologies.
It should be mentioned that only data from the first two sensors were used for the experiments described in the reference publication. The data from other sensors can also be used by user for research, development, and testing in face-PAD provided that they agree to the corresponding EULA.
| Table 1.1: Sensor description for WMCA data collection | ||||
| Sensor | Channel | Resolution | Frame rate (approx.) | Used in the reference publication |
|---|---|---|---|---|
|
Intel RealSense SR300
|
Color | 1920 x 1080 | 30 fps | Yes |
|
Intel RealSense SR300
|
Depth | 640 x 480 | 30 fps | Yes |
|
Intel RealSense SR300
|
Infra-red | 640 x 480 | 30 fps | Yes |
|
Seek Thermal Compact PRO
|
Thermal | 320 x 240 | 15 fps | Yes |
|
Xenics Gobi-640-GigE
|
Thermal | 640 x 480 | 25 fps | No |
| uEye SE USB2.0 | Infra-red | 1280 x 1024 | 15 fps | No |
The data was captured during several sessions with different environmental conditions. Session 4 was dedicated to presentation attacks only. The information about the sessions can be found in Table 1.2.
| Table 1.2: Session description for WMCA data collection | ||
| Session | Background | Illumination |
|---|---|---|
| 1 | uniform | ceiling office light |
| 2 | uniform | day-light illumination |
| 3 | complex | day-light illumination |
| 4 | uniform | ceiling office light |
| 5 | uniform | ceiling office light |
| 6 | uniform | side illumination with LED lamps |
| 7 | complex | ceiling office light |
Presentations
The presentations in the database can be grouped into different categories:
1. Bonafide: Includes bonafide data from participants with and without medical glasses. Some participants were asked additionally to wear a pair of unisex glasses with black rim that had no correction (Fig. 1.2). The PPG data was captured only once, mostly when the participant did not wear any glasses.

Figure 1.2: The unisex glasses with no correction used in some of the bonafide recordings.
2. Glasses: Different models of disguise glasses with fake eyes (funny eyes glasses) and paper glasses. These attacks constitute partial attacks (Fig. 1.3).

Figure 1.3: Sample images of glasses used as presentation attacks.
3. Fake head: Several models of mannequin heads were used, some of the mannequins were heated with a blower prior to capture (Fig. 1.4).

Figure 1.4: Sample images of mannequin heads.
4. Print: Printed face images on A4 matte and glossy papers using professional quality Ink-Jet printer (Epson XP-860) and typical office laser printer (CX c224e). The images were captured by the rear camera of an “iPhone S6” and re-sized so that the size of the printed face is human like.
5. Replay: Electronic photos and videos. An “iPad pro 12.9in” was used for the presentations. The videos were captured in HD at 30 fps by the front camera of an “iPhone S6” and in full-HD at 30 fps by the rear camera of the “iPad pro 12.9in”. Some of the videos were re-sized so that the size of the face presented on the display is human like.
6. Rigid mask: Custom made realistic rigid masks and several designs of decorative plastic masks (Fig. 1.5).

Figure 1.5: Sample images of rigid masks.
7. Flexible mask: Custom made realistic soft silicone masks (Fig. 1.6).

Figure 1.6: Sample images of flexible masks.
8. Paper mask: Custom made paper masks based on real identities. The masks were printed on the matte paper using both printers mentioned in the print category (Fig. 1.7).

Figure 1.7: Sample images of paper masks.
9. Wig: Several models of wigs for men and women (Fig. 1.8).

Figure 1.8: Sample images of wigs.
10. Makeup: Regular makeup materials were used on the face to increase the apparent age of the participants. The design is called “Old Age” makeup. The makeup was performed gradually and the data was captured several times during the process resulting in different intensity of makeup for most of the participants. No prosthetics were used in the makeup process (Fig. 1.9).

Figure 1.9: Sample images of old age makeup with different intensities. The image on the left is without makeup and the intensity of makeup increases from left to right.
It should be mentioned that the data from “Wig” and “Makeup” category were not used for the experiments described in the reference publication, however they can be accessed similar to the other categories.
The number of presentations in the database can be found in Table 1.3.
| Table 1.3: Statistics for WMCA database | |
| Category | Number of presentations |
|---|---|
| Bonafide | 347 |
| Glasses | 75 |
| Fake head | 122 |
| 200 | |
| Replay | 348 |
| Rigid mask | 137 |
| Flexible mask | 379 |
| Paper mask | 71 |
| Wig | 46 |
| Makeup | 216 |
| TOTAL | 1941 |
Evaluation
All four channels of data obtained from “Intel RealSense SR300” and “Seek Thermal Compact PRO” are used in the reference publication. Since the consecutive frames are correlated, only 50 frames from each video were selected. The frames are uniformly sampled in the temporal domain. The total number of 1679 presentations including bonafide and presentation attacks were grouped into three subsets, train, dev, and eval. Data from “Wig” and “Makeup” category was not used in the experiments. The data split is done ensuring almost equal distribution of PA categories and disjoint set of client identifiers in each set. Each of the PAIs had different client id. The split is done in such a way that a specific PA instrument will appear in only one set. A low level database interface is implemented that handles loading and spatial and temporal alignment of the data 1. The preprocessed images for the data used in the experiments are also provided. The preprocessed method is described in details in the reference publication and the implementation is available publicly 2. The number of presentations in train, dev, and eval subset for the grandtest protocol of the reference publication is mentioned in Table 1.4.
| Table 1.4: Statistics for train, dev, and eval subset of grandtest protocol | |||
| Subset | Bonafide | Presentation Attack | Both |
|---|---|---|---|
| train | 124 | 441 | 565 |
| dev | 108 | 449 | 557 |
| eval | 115 | 442 | 557 |
| TOTAL |
347 |
1332 |
1679 |
Some example images are illustrated from different channels (Fig. 1.10), different sessions (Fig. 1.11) , and different presentation attacks (Fig. 1.12). An example of preprocessed data from four channels is also provided in Fig. 1.13.

Figure 1.10: Sample images of a) bonafide and b) flexible mask attack from the database for all channels after alignment. The images from all channels are aligned with the calibration parameters and normalized to eight bit for better visualization.
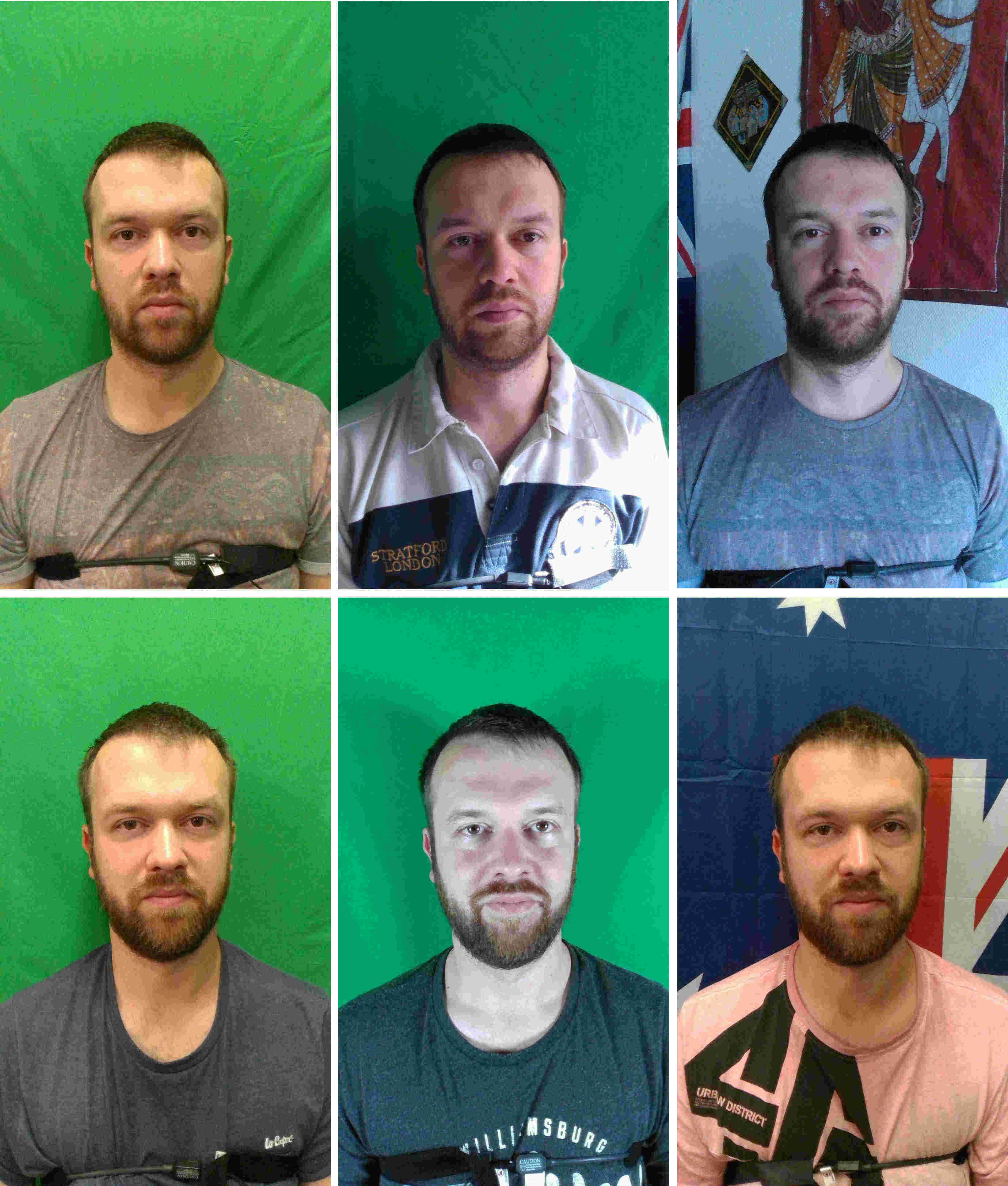
Figure 1.11: Examples of bonafide data in 6 different sessions. Top left is session one and bottom right is session seven. There is no bonafide data for session four.

Figure 1.12: Examples of presentation attacks with different PAIs. (a): glasses (paper glasses), (b): glasses (funny eyes glasses), (c): print, (d): replay, (e): fake head, (f): rigid mask (Obama plastic Halloween mask), (g): rigid mask (transparent plastic mask), (h): rigid mask (custom made realistic), (i): flexible mask (custom made realistic), and (j): paper mask.

Figure 1.13: An example of preprocessed data from four channels is provided in Fig. 1.13

Figure 1.14: An examples of preprocessed data from color channel for different bonafide is shown in Fig. 1.14
1 https://gitlab.idiap.ch/bob/bob.db.batl
2 https://gitlab.idiap.ch/bob/bob.paper.mccnn.tifs2018
File Naming Convention
<client_id>_<session_id>_<presenter_id>_<type_id>_<pai_id>.hdf5
- client_id: This three digit number presents the identity of what is presented to the system. For bonafide, it is the ID given to the subject upon arrival and for the attacks, it is a number given to a PAI. Please note that if the identity of a subject is the same as the identity of a PAI, this number is the same for both cases. One example is the silicon masks. If a silicon mask is made from subject ‘x’s’ face and subject ‘x’ also participated as bonafide in the data collection the ‘client_id’ for bonafide and silicon mask is the same.
- session_id: A two digit number given to a session as mentioned in Table 1.2.
- presenter_id: It is a three digit number that identifies who is presenting the attack to the system. If a subject is presenting an attack to the system, this number is the subject’s ‘client_id’. If the attack is presented on a support, this number is ‘000’. If the data is bonafide this number is ‘000’ as well since there is no presenter in this case.
- type_id: A one digit number describing the type of the attack presented to the system. The 7 mentioned attack types are grouped into 4 categories, namely, `facial disguise`, `fake face`, `photo`, `video`, and `makeup`. The detailed information about this regrouping is available as open source code[1]. For bonafide the ‘type_id’ is ‘0’.
- pai_id: A three digit unique number associated with each and every PAI. This number for bonafide with no medical glasses is ‘00’, for bonafide with medical glasses is ‘01’, and for bonafide with unisex glasses is ‘02’.
Here are some examples for more clarification:
- - 035_01_000_0_00.hdf5 : This is the bonafide file of client number 035 in session number 1 when they did not wear medical glasses.
- - 005_01_000_0_01.hdf5 : This is the bonafide file of client number 005 in session number 1 when they did wear medical glasses.
- - 530_03_001_2_18.hdf5 : This is a fake face attack where the identity 530 is presented to the camera by client number 001 in session 03.
- - 018_02_000_3_10.hdf5 : This is a photo attack where the identity 018 is presented to the camera using stand in session 02.
[1]: <https://gitlab.idiap.ch/bob/bob.db.batl/blob/master/bob/db/batl/batl_config.py>